Remember the times when it was enough to just change your IP through a VPN? Now platforms like Facebook read so much data from your device that it'd be enough for a secret service dossier. Phone model, firmware version, installed apps, even the quirks of your gyroscope - everything's fair game. Android antidetect has transformed from an exotic tool to a basic survival instrument in digital. Especially if you're working with dozens of accounts and don't want to wake up to a red screen saying "Your account has been blocked."
What is an antidetect browser on mobile
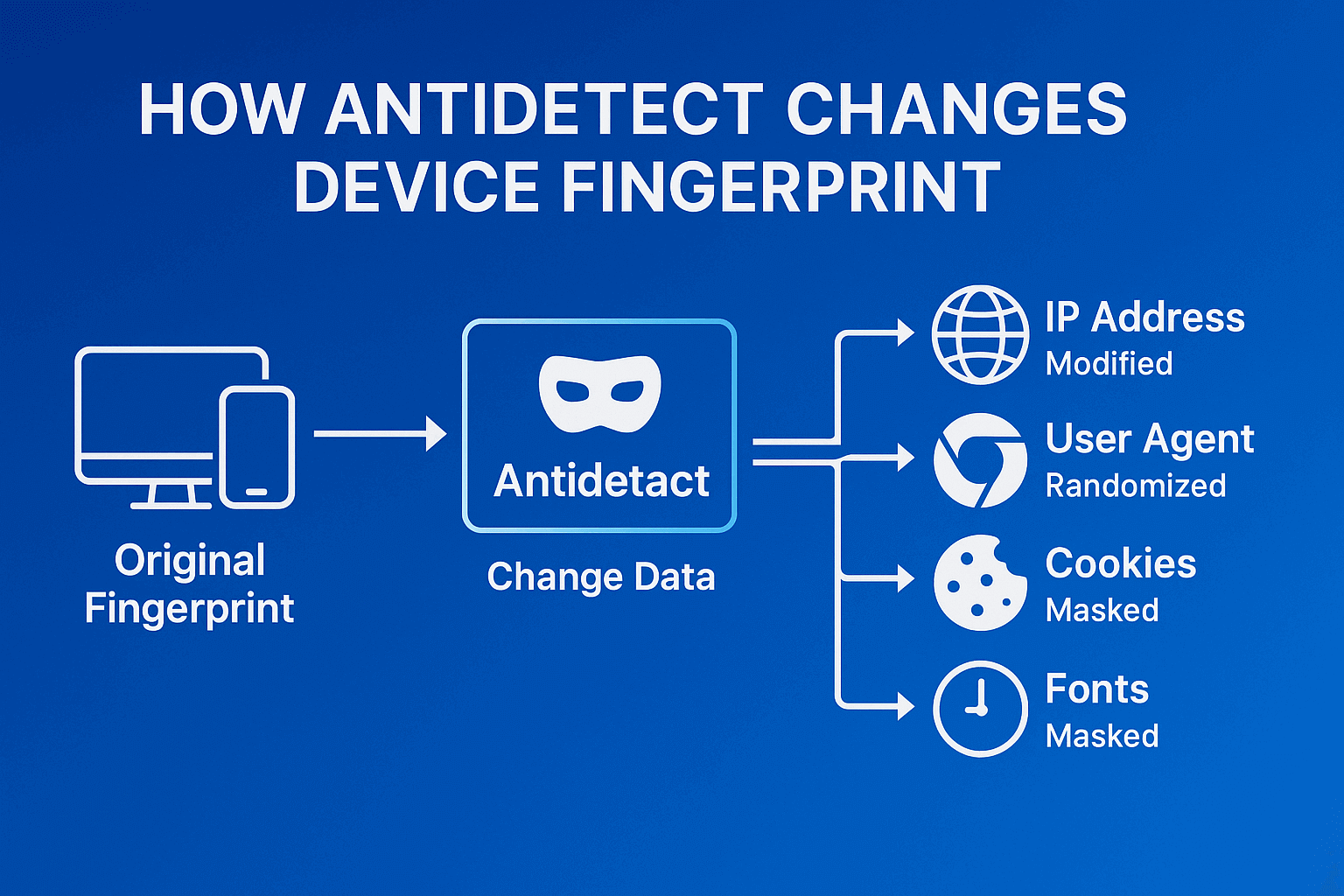
Definition and how it works
Picture this situation: you walk into a store, and the security guard photographs not just your face, but your shoes, your gait, the way you hold your phone. Tomorrow you come in a wig and different clothes - useless, they'll recognize you by dozens of little details. That's how modern tracking systems work.
An antidetect browser for phones changes these "little things." It feeds websites fake data about your device. Had a Samsung Galaxy S23 with Android 13? Now you're the happy owner of a Xiaomi Redmi Note with Android 11. And it's not just the name that changes. Antidetect browser android fakes hundreds of parameters - from screen size to the list of installed codecs.
How mobile antidetect differs from desktop
Desktop versions work in greenhouse conditions. Windows or MacOS give developers plenty of room to maneuver. Android antidetect has to work around the rigid constraints of mobile OS.
Take a simple example. On a computer, antidetect can create a completely isolated environment for each profile. On a phone? You have to hack around access permissions, bypass sandbox restrictions, fight with "helpful" battery optimization that kills background processes.
iPhone antidetect operates in straight-up prison conditions. Apple controls iOS so tightly that developers have to make compromises. Many features are simply unavailable without jailbreak, and with it, you automatically fall under suspicion from all serious services.
Emulators vs. native apps
The eternal debate - which is better? With Android antidetect emulator, you get an army of virtual phones on one PC. Fire up 50 BlueStacks windows, assign each its own proxy - and off you go farming accounts. Sounds tempting until you hit reality.
Modern platforms detect emulators through dozens of tells. Signs that distinguish an emulator from a real phone:
- Sensors. A real smartphone has an accelerometer, gyroscope, proximity sensor, light sensor, and others. Emulators usually don't transmit data from them or return "empty" values.
- Graphics. Virtual devices might show suspiciously high, "perfect" performance - like stable 60 FPS without drops even in heavy games. That's not typical for real phones.
- System calls. Apps can make "test" queries to the system. On an emulator, responses will differ from what a real device gives (for example, when working with camera, GPS, or SIM card).
Antidetect emulators try to mimic the imperfections of real devices to look "alive" to antifraud systems. Among the most popular tricks:
- Artificial lag - the emulator intentionally adds delays when opening apps, clicking, or swiping, so behavior looks like a regular phone, not a perfect virtual machine;
- Noise in accelerometer data - real sensors don't output perfectly smooth values, so the emulator adds microscopic fluctuations, imitating the natural tremor of a hand holding the device;
- Fake battery drain - the system sees charge gradually decreasing with use, like on a real smartphone, instead of staying at 100% all the time;
- Processor temperature - some emulators fake heating data to show "natural load";
- Network instability - small ping or speed drops that usually happen with real mobile carriers.
So the emulator looks not like a "perfect machine," but like a regular user device with all its minor flaws.
Native apps on real hardware look maximally natural: no emulation, everything's like a real user. Plus - high antifraud trust level. Minus - scaling is expensive and complicated: keeping dozens or hundreds of phones is already a separate farm.
The solution depends on your tasks: if you need quick launch and testing - emulators work. If you're betting on long-term farming with fewer risks - real hardware is more reliable.
GonzoProxy team's opinion: for working with residential proxies, we see the optimal choice in native apps, because real device + real IP gives the best balance between security and stability.
Contents
- What an Anonymous Proxy Service Represents
- How an Anonymous Proxy Works
- Proxy Anonymity Levels
- Types of Anonymous Proxies
- Main Benefits of Using Anonymous Proxies
- Risks and Limitations
- How to Set Up and Use an Anonymous Proxy
- Solving the "Anonymous Proxy Detected" Error
- How to Choose a Reliable Anonymous Proxy Service
- FAQ
- Conclusion
- VPN and Proxy: Key Differences
- What is a Proxy Server?
- What is VPN?
- Security and Privacy
- Speed and Performance
- When Should You Use a Proxy Server?
- When Should You Use VPN?
- Is It Worth Using VPN and Proxy Together?
- Mistakes When Choosing Between VPN and Proxy
- Busting Myths About VPN and Proxy
- VPN or Proxy: How to Choose the Right Option?
- FAQ
- Conclusion
- What is a proxy server for Google Chrome and why do you need it
- How proxy works in Chrome browser
- Ways to configure proxy in Google Chrome
- Setting up proxy in Google Chrome through Windows
- Setting up proxy in Google Chrome through macOS
- Setting up proxy for Chrome through extensions
- Setting up proxy in Chrome on Android
- Setting up proxy in Chrome on iPhone and iPad
- Connection check and speed test
- Typical errors when working with proxy in Chrome
- FAQ
- Conclusion
- Why you need proxies for Reddit
- Why Reddit might be blocked
- What restrictions does Reddit have
- Who needs proxies and how they help
- What you can do with proxies for Reddit
- How to choose the right type of proxy for Reddit
- Proxy vs VPN for Reddit
- How to set up and use proxies for Reddit
- Top proxy providers for Reddit in 2025
- Common problems and solutions
- Practical use case scenarios
- FAQ
- Conclusion
- Why LinkedIn requires using proxies
- How proxies help in working with LinkedIn tools
- Types of proxies for LinkedIn and selection criteria
- 10 best proxy providers for LinkedIn
- Setting up and using proxies
- Tips for safe LinkedIn outreach scaling
- FAQ
- Conclusion: how to build a stable system for working with LinkedIn through proxies
- How Amazon detects and blocks proxies
- Benefits of using proxies for Amazon
- Which proxy types work best for Amazon
- Best residential proxy providers for Amazon (2025)
- Key features of a good Amazon proxy provider
- How to set up a proxy for Amazon
- Common problems when working with proxies on Amazon
- How to use Amazon proxies for different tasks
- Best practices for safe Amazon proxy usage
- FAQ
- Conclusion – choose stability, not quantity
- Step 1 — Download and Install VMLogin
- Step 2 — Create a New Browser Profile
- Step 3 — Get Your Gonzo Proxy Credentials
- Step 4 — Configure Proxy Settings in VMLogin
- Step 5 — Verify Proxy Connection
- Step 6 — Launch Your Browser Profile
- Step 7 — Optional: Set Up Multiple Profiles / Rotating Sessions
- Step 8 — Troubleshooting Common Issues
- Step 9 — Start Automating with Gonzo Proxy + VMLogin
- What is an anonymizer in simple terms
- How anonymizers differ from proxies and VPNs
- How an anonymizer works
- Types of anonymizers and anonymity levels
- How to format proxies for working with anonymizers
- How to use an anonymizer to access blocked sites
- Advantages and risks of using anonymizers
- How to choose an anonymizer or proxy for your tasks
- FAQ
- Conclusion
- How to sell quickly and effectively on Avito
- What is mass posting on Avito and why you need it
- Manual and automated mass posting
- Multi-accounting: how to manage multiple accounts on Avito
- Step-by-step launch plan
- How not to get banned with mass posting and multi-accounting
- Mass posting vs alternative sales methods
- FAQ
- Conclusion
- Why TikTok gets blocked and doesn't always work with VPN
- How proxies and VPN differ for TikTok
- When it's better to choose VPN for TikTok
- When it's better to choose proxy for TikTok
- How to set up proxy for TikTok (short instruction)
- Risks and precautions when working with TikTok through VPN and proxies
- FAQ
- Conclusion
- What does transparent proxy mean
- How transparent proxy works in a real network
- Spheres of application for "invisible" proxy
- Advantages and disadvantages of transparent proxy
- Setting up transparent proxy: step by step
- Are transparent proxies secure
- Popular solutions for transparent proxy setup
- Checklist for working with transparent proxies
- FAQ
- Conclusion
- Why proxies are a must for Dolphin Anty
- Types of proxies you can connect to Dolphin
- Rotating vs Static
- Step-by-Step: How to Add a Proxy in Dolphin Anty
- Common proxy connection errors and fixes
- How to choose reliable proxies for Dolphin Anty
- Tips for optimizing costs
- Practical cases of using Dolphin Anty with proxies
- FAQ
- Final thoughts
- Types of proxies used for parsing
- How to choose proxies for parsing
- Setting up and rotating proxies for parsing
- Technical tricks for bypassing blocks
- Practice: building a proxy pool for parsing
- Metrics and monitoring parsing quality
- Best practices and ready solutions
- FAQ
- Summary: Which proxy to choose for parsing
- How proxies work in traffic arbitrage
- Types of proxies for arbitrage and their features
- What problems do proxies solve in arbitrage
- Top proxy providers for arbitrage in 2025
- Comparison table of proxy providers
- How to pick the right proxies for arbitrage
- How to set up proxies for arbitrage
- Safe proxy usage tips
- FAQ
- Conclusion
- What are residential proxies needed for?
- How do residential proxies work?
- How do residential proxies differ from others?
- Connecting residential proxies from GonzoProxy
- Examples of using GonzoProxy residential proxies in Python
- Pros and cons of residential proxies
- How to check residential proxies
- Common usage errors
- FAQ
- Conclusion
- Why does Facebook often block accounts and cards?
- Why use a virtual card for Facebook Ads?
- Multicards.io — a trusted virtual card service for Meta Ads
- Should you buy or create Facebook ad accounts?
- Why proxies are essential
- What kind of proxies are best for Facebook Ads?
- GonzoProxy — premium residential proxies for Facebook Ads
- How to safely link a virtual card to Facebook Ads
- Final recommendations
- What’s a DePIN farm and why should you care?
- So, what exactly is DePIN?
- Other DePIN projects already killing it
- What do you need to start your DePIN farm?
- How to create profiles and set up the antidetect browser
- How to choose and set up a proxy?
- What about Twitter/X accounts?
- How to get email accounts?
- Before you launch — one last tip!
- How to properly chain your accounts?
- How modern fraud detection systems track violators
- Google Ads: anti-fraud specifics in 2025
- How to tell your proxies aren't working?
- Why most proxies no longer work with ad platforms
- How to select and verify proxies for ad platforms
- Strategy for stable operation with ad platforms
- Conclusion: don't skimp on infrastructure
For advertisers and marketers
Know how much it costs to restore a banned ad account with history and high trust? The right answer - it's cheaper to prevent the ban. Arbitrageurs running gambling or nutra keep 20-30 Facebook accounts. One fingerprint mistake - and the whole chain gets banned.
SMM folks use antidetect browser for android for less dramatic but equally important tasks. Boosting? Yes, but smart. Not dumb bots with identical behavior, but "live" users with unique devices. Crowdfunding, dropshipping, even basic management of corporate account groups - masking is needed everywhere.
CPA networks especially watch traffic sources closely. Running from one device under different masks? Get ready to lose 90% of conversions. But with properly configured anti-detect system, each flow looks organic.
For freelancers and remote workers
Upwork bans you for trying to create a second account faster than you can fill out the profile. Meanwhile, competition is so fierce that one profile is a dead end. Top freelancers keep 3-5 accounts for different specializations. Antidetect browser lets you be simultaneously a "Senior Python Developer from Poland" and a "UI/UX designer from Argentina."
Remote workers face another problem. Company requires working only from certain countries? Going on vacation to Thailand but don't want to lose access to corporate systems? Mobile antidetect solves this more elegantly than dragging a laptop with configured VPN.
For developers and testers
QA engineer needs to test app behavior on iPhone 12 (Brazil), Samsung A52 (India), and Pixel 6 (USA). While the region itself doesn't change the base OS, it affects builds, preinstalled apps, carrier settings, and locales. Instead of buying devices and flights, you can use android antidetect that emulates device, IMEI, SIM provider, GPS, and local settings - giving realistic sets of test conditions.
Data parsing is a whole other story. Google returns different search results depending on device. Amazon shows different prices. Instagram serves different content. Without rotating devices and locations, you'll get a distorted picture.
For gamers and hustlers
After February 2022, thousands of services became unavailable from Russia. PayPal, Spotify, ChatGPT - the list goes on. Antidetect browser for android paired with decent proxies brings back access to civilization.
Gamers discovered a new world. Referral programs paying $50 for each friend brought in? Create 20 "friends" and cash out a thousand bucks. Morally questionable but technically elegant. Account farming for resale has become a million-dollar industry.
For example, in 2023 one referral program paid $50 per referred user. Take a residential proxy from Brazil for $8, add transaction fee $2 - and voila, you're up $40 per account. On a hundred such "friends" that's already $4,000 clean.
That's why profitable proxies aren't just an expense but a money-making tool. At GonzoProx you can grab residential IPs for such tasks and not worry about margin - it stays with you, not the provider.
GoLogin Mobile - multi-accounting, PC sync
The GoLogin guys bet on ecosystem. Created a profile on computer - it's automatically available on phone. The fingerprint database updates weekly, which is critical for bypassing new detection methods.
The feature - "cloning" mode. You capture the fingerprint from a friend's real device and use it as a template. Facebook sees a familiar device and relaxes. Costs from $49/month, but for serious work - peanuts.
Kameleo Mobile - flexible fingerprint spoofing, API integration
Kameleo - the techie's choice. REST API lets you automate everything from profile creation to proxy rotation. Write a script - and let it work while you sleep.
The special thing - protection from advanced detection methods. WebGL fingerprinting, AudioContext API, even JavaScript engine behavior analysis - Kameleo masks it all. True, it costs accordingly - from €59/month.
Dolphin Zero - privacy and auto-cleanup
Minimalist solution for the paranoid. No saved profiles, no history. Each session - clean slate. Open, work, close - all traces destroyed.
Good for one-off operations. Need to check a competitor's site as a regular user? See how your ad looks from another country? Dolphin Zero handles it. Inconvenient for regular account work - profiles don't save.
Brave / Firefox Focus / DuckDuckGo - when simplicity matters
These aren't antidetects in the full sense. More like privacy-enhanced browsers. They block trackers, clean cookies, hide some fingerprints. Too weak for serious work, but fine for basic needs.
Brave is interesting for its built-in crypto rewards system. Firefox Focus doesn't save any data at all. DuckDuckGo blocks trackers at the app level, not just in browser. All free, which hooks newbies.
TOR browser for iOS and Android - anonymity with speed limitations
Tor - the grandfather of anonymity. Traffic bounces through three random servers before reaching its destination. Practically impossible to track. But there are catches.
Speed - like dial-up from the 90s. Half the sites show captcha or block Tor exit nodes entirely. Absolutely unsuitable for Facebook or Google Ads - you'll get flagged instantly. But for truly sensitive tasks, few alternatives exist.
Connecting proxies (HTTP, SOCKS5, mobile IPs)
Proxies are like a house foundation. Skimp on quality - the whole building collapses. HTTP proxies work for web surfing but get caught on complex checks. SOCKS5 is more universal, works with any protocols.
Mobile IPs - the 2025 gold standard. Platforms trust traffic from mobile carriers more than home connections. Simple logic: scammers rarely bother buying SIM cards. GonzoProxy offers mobile IPs with manual replacement if the proxy gets detected.
Setup takes minutes. In antidetect:
1. Create new profile or edit existing one
2. In "Proxy" section choose "Custom" or "Manual setup"
3. Select HTTP/SOCKS5 type, enter pre-obtained data
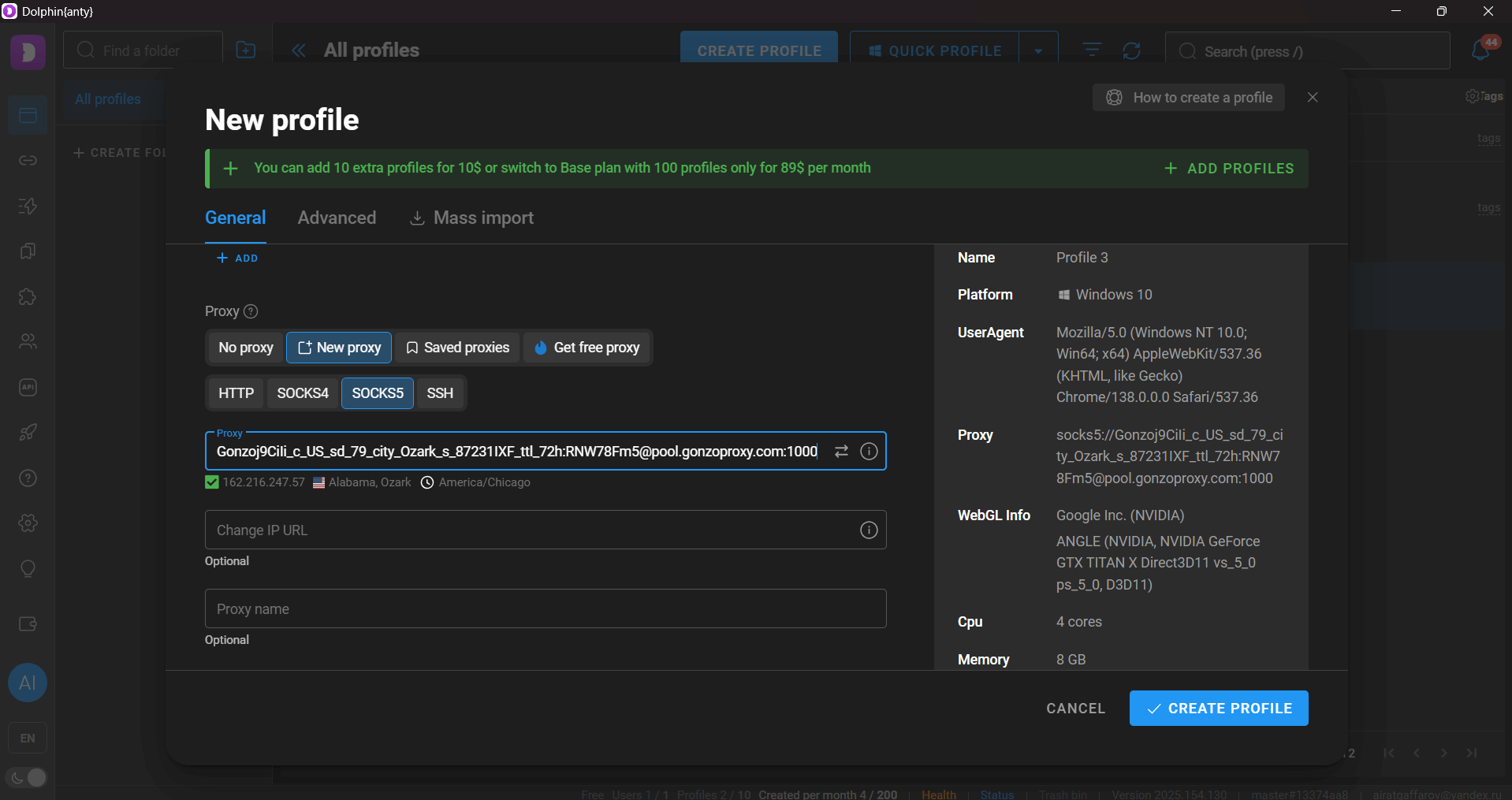
4. Test connection and save profile
Working with profiles and cookies
Each profile - separate identity. Ivan from Moscow can't suddenly become João from São Paulo. Follow the logic: system language, timezone, screen resolution should match the legend.
Cookies - account memory. Export them after each important session. Antidetect crashed, phone drowned - no problem, restore profile from backup in minutes. Store cookies encrypted, preferably in cloud with two-factor authentication.
Integration with emulators (Android emulator, iOS sandbox)
BlueStacks is good for beginners - simple interface, stable operation. LDPlayer is built for gaming but arbitrageurs appreciate it too. NoxPlayer allows fine-tuning hardware parameters.
Key point - changing identifiers. IMEI, Android ID, MAC address must be unique for each profile. Use generators with validity checking - random digits won't cut it.
For iOS the situation's tougher. Official Xcode simulator only works on Mac. Third-party solutions either require jailbreak or cost like a used car.
Automation via API and scripts
Manual work is for newbies. Pros automate routine. Example simple Python script for mass profile creation:
import requests
import random
def create_profile(name, country):
proxy = get_proxy(country) # Get proxy for needed country
device = random.choice(devices[country]) # Choose popular device
profile_data = {
"name": name,
"proxy": proxy,
"device": device,
"timezone": get_timezone(country),
"language": get_language(country)
}
response = requests.post("https://api.antidetect.com/profiles",
json=profile_data,
headers={"API-Key": "your_key"}
)
return response.json()Set it up once - works for months. Main thing, don't forget to update device and proxy lists.
Why free browsers aren't reliable
You know where free cheese is. Developers need to make money somehow. Three options: ads, selling your data, or using your device for their purposes.
Seen an antidetect requesting weird permissions? Access to contacts, SMS, microphone? Run away. Best case they'll sell data to marketers. Worst case - they'll use your phone for botnets or mining.
Another problem - rare updates. Facebook changes detection algorithms every two weeks. Free antidetect updates once every six months. Guess who wins that race?
What are the risks when working with ad accounts
$50,000 balance in an ad account isn't rare for big arbitrageurs. Losing that sum due to a stupid mistake - nightmare fuel.
Typical ban triggers: sudden geo change (New York morning, Bangkok evening), payment data and location mismatch, using one card for dozens of accounts. Facebook's machine learning systems analyze hundreds of behavior parameters. Even cursor movement speed can give away a bot.
Mistakes when choosing proxies for antidetect
Datacenter proxies for $0.1 - road to failure. Their IPs have long been on every serious platform's blacklist. Public proxies are even worse - your neighbors will be spammers, carders, and other characters.
Rotation should be smart. Changing IP every 5 minutes - suspicious. Keeping one address for weeks - dangerous if it gets banned. Optimal - sticky session for 24-48 hours with manual change option when needed.

Quality proxies turn antidetect from a toy into a serious tool. GonzoProxy specializes in tasks where IP cleanliness is critical.
Clean IPs for reducing blocks - P2P network of 20+ million real devices. These aren't some servers in a datacenter basement, but real computers and smartphones of regular users. Facebook sees an Ohio housewife's IP, not another bot.
Rotation and sticky sessions for uninterrupted work - smart IP retention system. While the donor device is online, you work from one address. Disconnected - system automatically picks a similar one from the same city and provider. No session breaks.
Geo-targeting by country/city/provider - want an IP from Comcast in Dallas? You got it. Need Vodafone from Manchester? No problem. 150+ countries, 2000+ cities, hundreds of providers. And no extra charges for precise targeting - it's included in the base cost.
Integration through dashboard - connection in 30 seconds. Copy proxy data, paste into antidetect, work.
✓ Does it support Android/iOS versions you need? Check not just current OS version but update plans. iOS 18 coming in six months - will there be support?
✓ Can you connect external proxies? If antidetect only works with its own proxies - that's vendor lock-in. They'll jack up prices, quality will drop, and you can't do anything.
✓ Is there automation (API, scripts)? Without API you'll be clicking like it's 2010. Fine for 5 accounts, torture for 50.
✓ How does it work with emulators and antidetect plugins? Compatibility with BlueStacks, LDPlayer, NoxPlayer expands possibilities. You can work from both phone and computer.
✓ Check reviews and updates - is the project alive? Last update a year ago? Forum dead? Developers vanished? Find another option.
✓ Trial period or demo version - normal services let you try. At least 3 days or 100 MB traffic. If they demand yearly payment upfront - be suspicious.
✓ Technical support - message support before buying. If they reply a week later with a template response, imagine what happens after you pay.
FAQ
Mobile antidetects have evolved from janky tools to professional instruments. Today an antidetect browser for iPhone or Android is a must-have for anyone making more online than at a regular job.
Choosing a specific solution depends on tasks and budget. Beginners can use simple options like Brave with basic proxies. Professionals need GoLogin or Kameleo with premium residential IPs.
GonzoProxy solves the quality proxy question. Traffic doesn't expire, IPs are clean, support actually helps instead of sending templates. Use promo code WELCOME15 for 15% off your first order. Start with a small volume, test on your tasks, scale as you grow.